Category Archives: Safe Computing
History of Surveillance Timeline on Safe Computing
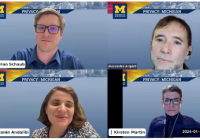
Privacy@Michigan takes over Michigan Theater with 1984 screening and faculty panel
Privacy@Michigan speakers discuss the economics of privacy
The annual celebration of Data Privacy Day at the University of Michigan kicked off with a Privacy@Michigan keynote event featuring Prof. Alessandro Acquisti, Trustees Professor of Information Technology and Public Policy at Carnegie Mellon University’s Heinz College, and the co-director of the CMU Center for Behavioral Decision Research (CBDR).
Black History Month 2024: An artist and writer examine surveillance
Black History Month pays “tribute to the generations of African Americans who struggled with adversity to achieve full citizenship in American society.” The Black History Month 2024 theme, “African Americans and the Arts,” explores the key influence African Americans have had in the fields of “visual and performing arts, literature, fashion, folklore, language, film, music, architecture, culinary and… Read More »
Duo releases a new look to all customers — coming to U-M Feb. 20
On Tuesday, February 20, 2024, the University of Michigan will start using an updated Duo Universal Prompt screen for two-factor authentication. All Duo customers across the world, including U-M, are required to transition to the Universal Prompt, and Duo is ending support for the traditional version.
Happy Secure Holidays from IA
The holidays are a great time for shopping and travel, but they are also prime time for cybercrime. ITS Information Assurance (IA) wants to gift you some Safe Computing tips to protect your personal data this holiday season. Secure your devices These basics will help you start out from a more secure place: Shop securely After you take… Read More »
Enhanced confidentiality of information on ITS Websites
Information and Technology Services (ITS) is reviewing more closely all technical service information published publicly. In the spirit of an open, higher-education environment, much of the documentation and content published by ITS has been accessible to the public, even when only intended for the U-M community. Going forward, the ITS approach will be to limit access to some… Read More »
A farewell to Cosign
On November 1, 2023, the ITS Identity and Access Management (IAM) team and colleagues across ITS and the university gathered to celebrate the retirement of the Cosign service at U-M. Created by members of U-M’s IT Commons group in 2001, Cosign was a web-based, single-sign-on solution that was rapidly adopted at other universities. As U-M’s Cosign reached the… Read More »
Safe Computing: Copyright Compliance
Ways to Step Up Security
Visit Safe Computing
Ever wonder what makes a good password? How you can spot phishing before you’re caught by it? Or maybe you’re just curious about what’s new in the world of IT security and privacy? For all of this and much more, visit the Safe Computing website. Safe Computing is an authoritative website filled with IT security and privacy guidance… Read More »
U-M requiring password reset for all UMICH (Level-1) accounts
The University of Michigan has mandated that passwords for all UMICH (Level-1) accounts be changed by the end of Sept. 12. An email informing faculty, staff and students across the Ann Arbor, Dearborn and Flint campuses, as well as Michigan Medicine, was sent from Ravi Pendse, vice president for information technology, and Sol Bermann, chief information security officer.… Read More »
Cosign retirement success
Originally designed at U-M more than twenty years ago, Cosign was once widely used across higher education. The degree to which U-M had integrated Cosign into countless applications was a testament to its success. However, the user base dwindled at U-M and across higher ed as institutions transitioned to more modern authentication protocols (OIDC and SAML). At U-M… Read More »
Upcoming changes to Duo two-factor authentication
Duo has released a new Universal Prompt to replace their traditional two-factor authentication prompt that U-M currently uses. ITS Identity and Access Management (IAM) is planning to switch U-M Weblogin to use the Duo Universal Prompt in early 2024. Visit the Upcoming Changes to Duo page on Safe Computing to see an example. The advantages of the Universal… Read More »
TikTok, Boom. documentarian earns Emmy nom
ITS congratulates Shalini Kantayya on her 2023 News & Documentary Emmy nomination for her documentary TikTok, Boom. This is her second Emmy nomination. Kantayya directs “fiction and nonfiction films that artfully marry the future of science with the future of story.” (shalinikantayya.net) ITS hosted a conversation with Kantayya about TikTok, Boom. for a Dissonance event earlier this year.… Read More »
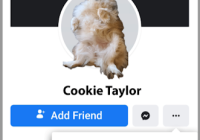
Social media scams: Fake friends
“I’ve been hacked! Don’t accept friend requests from me!” Most of us on social media see that warning periodically, and while not entirely accurate, it’s a sign of how prevalent fake friend requests are. These scams are rarely a sign of actual “hacking” – gaining unauthorized access to the account itself – but they do involve a little… Read More »
Practice and encourage good digital citizenship
Whether you are sending email, participating in online discussions, or posting to social media, practicing good digital citizenship makes the online world safer and more enjoyable for yourself and others. Do your part to support online civility and promote good digital citizenship. Some practical tips are to: Refer to the following web pages for more guidance and links… Read More »
Security tips for using public WiFi
Online Safety for the LGBTQ Community
Though there has been much progress towards LGBTQ equality, this community has inherent risks online that other communities do not face. As experts in Cybersecurity, and strong LGBTQ allies, ITS Information Assurance wants to ensure those at risk of online harassment and crime have the information they need to protect themselves.