Author Archives: Matt Ranville, ITS Privacy Office
Celebrating Data Privacy Day 2025
Stay Safe This Holiday Season
New CrowdStrike Falcon Sensor Status Icon for Windows
Security Tips for Using Public WiFi
Vulnerability Scanning and Blocking of Unremediated Systems
Happy Secure Holidays from IA
The holidays are a great time for shopping and travel, but they are also prime time for cybercrime. ITS Information Assurance (IA) wants to gift you some Safe Computing tips to protect your personal data this holiday season. Secure your devices These basics will help you start out from a more secure place: Shop securely After you take… Read More »
Visit Safe Computing
Ever wonder what makes a good password? How you can spot phishing before you’re caught by it? Or maybe you’re just curious about what’s new in the world of IT security and privacy? For all of this and much more, visit the Safe Computing website. Safe Computing is an authoritative website filled with IT security and privacy guidance… Read More »
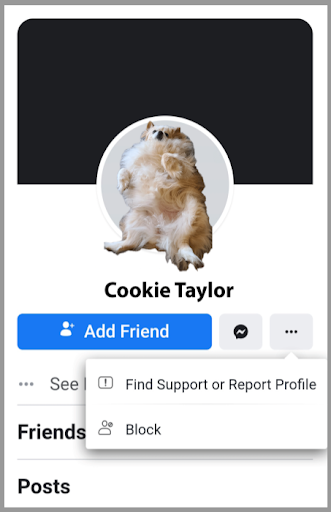
Social media scams: Fake friends
“I’ve been hacked! Don’t accept friend requests from me!” Most of us on social media see that warning periodically, and while not entirely accurate, it’s a sign of how prevalent fake friend requests are. These scams are rarely a sign of actual “hacking” – gaining unauthorized access to the account itself – but they do involve a little… Read More »
Security tips for using public WiFi
Social media scams: Some lost pets aren’t what they seem.
Few things tug at our hearts like adorable animals in danger or the distraught humans who miss them. Most of us have seen posts on social media from pet owners trying frantically to bring a lost furry family member home. They ask for help as simple as re-sharing, and we click, reposting that adorable dog we really hope… Read More »
Library of IT security and privacy awareness resources
The University of Michigan is committed to protecting the security of its information resources and the privacy of its students, faculty, and staff, but reaching community members with relevant and engaging information about cybersecurity and privacy can be a challenge. ITS Information Assurance (IA) has created a Library of resources to help our fellow Wolverines stay informed, create… Read More »
Biden Administration releases National Cybersecurity Strategy
New tools for SULs and Unit Security Partners
Information Assurance (IA) is committed to continually improving and streamlining capabilities, tools, and resources that support all of our shared responsibility to protect U-M systems and data. To this end, we are announcing changes to some key IA tools that will improve our unit partners’ ability to analyze and reduce security threats and risks for their units. New… Read More »