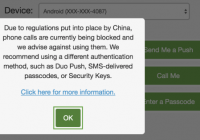
New Chinese restriction impacts Duo phone calls; Use other options
May 15, 2019 update: You can once again use the Call Me option to receive Duo phone calls to Chinese (+86) numbers for two-factor authentication. Automated phone calls for Duo two-factor authentication are no longer being blocked to Chinese (+86) numbers. Duo worked with one of its telephony providers and the Chinese government to resolve the issue. China… Read More »