Tips for secure passwords
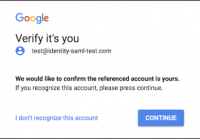
In honor of World Password Day on May 3, School of Information assistant professor Florian Schaub shared these online security tips: Use a password manager Use unique passwords Use two-factor authentication (like Duo!) Whether it’s World Password Day or not, it’s a good idea to update online privacy settings. Watch the video below to learn how. For additional… Read More »