Tag Archives: security
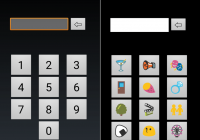
Emoji passwords
Would you rather unlock your smartphone with a plain four-digit PIN or with a series of emojis? For example, is it easier (and just more fun) to remember “🐱💦🎆🎌” than “2476”? Smartphone users commonly use emojis to express moods and emotions in emails and text messages. But there had been no formal study of how easy emoji passwords were to… Read More »
Smartphone security hole
A sweeping study by U-M researchers of an internet communication mechanism common in mobile devices has revealed that so-called ‘open ports’ are much more vulnerable to security breaches than previously thought. The vulnerability is most pronounced in Android apps that let users share data across devices and connect to their phones from their computers. One app, called Wifi… Read More »
‘Dissonance’ speakers discuss conflict & cyberspace
On April 13, a panel of experts discussed the development of international cyberspace norms. The event was part of the Dissonance, an ongoing speaker series that explores timely topics at the confluence of technology, law, privacy, and security. Watch the recording Event highlights Discussion points included what constitutes responsible state behavior in cyberspace, the differences between physical attacks and cyberattacks,… Read More »
‘Dissonance’ explores conflict & cyberspace April 13
As cyberspace becomes more and more central to the international security discussion, states are increasingly searching for common “rules of the road.” Attend the next Dissonance event and join Tim Maurer, fellow at the Carnegie Endowment for International Peace, as he moderates a panel discussion on the development of international cyberspace norms. The event is free and light… Read More »
‘Dissonance’ hosts Knight-Wallace fellows
Travel safely with technology
Whether you are planning a vacation or professional trip, you will likely take along smartphone, tablet, laptop, or other mobile device. Follow these tips to safeguard both your own—and the university’s—data. Before you travel Decide whether or not you need all your devices. If you don’t need it, leave it. Consider taking a device that you only use… Read More »
Review new sensitive data classifications
To support the proposed revision of the IT Security Policy, Information Assurance has published revised U-M Data Classification Levels on Safe Computing. The revised policy will be supported and supplemented by specific operational, procedural, and technical standards, many of which specify actions to take based on the classification level of the data involved. The new data classification levels… Read More »
Cyberwar strategy and game theory
Whether a nation should retaliate against a cyber attack is a complicated decision, and a new framework guided by game theory could help policymakers determine the best strategy. The “Blame Game” was developed in part by Robert Axelrod, a professor at the Ford School of Public Policy who is well known for solving a version of the classic… Read More »
Computer Showcase Tech Talks
Check out the upcoming Tech Talks from the Computer Showcase. All sessions will be held 11am – noon at the Computer Showcase location on the Ground Floor of the Michigan Union. March 24: Getting Started with Fitbit Need help choosing a fitness tracker? Whether you want to use heart rate data to take your fitness to the next… Read More »
Michigan Medicine tightens network security
Michigan Medicine is tightening the security for its wired and wireless networks to ensure that only authorized and inventoried computing devices can connect to internal resources. The network project is part of a year-long program to make the IT environment within the academic medical center as secure as possible for all patients, faculty, and staff. The program also… Read More »
Computer Showcase offers secure removable media
Computer Showcase now carries secure Aegis drives from Apricorn, providing encrypted removable media with layers of protection to keep sensitive data safe in transit. The Aegis Padlock Fortress is a 500GB USB 3.0 hard drive with 2 levels of military grade encryption, unique PIN access with programmable auto-lock features, and rugged physical attack protection. Aegis Secure Key offers… Read More »
“Musical virus” can hack smartphones
A security loophole that lets someone add extra steps to your Fitbit might seem harmless, but a group of computer security researchers at U-M and the University of South Carolina say it points to the broader risks that come with technology embedding itself into our lives. They found a vulnerability that allows them to compromise devices through the tiny accelerometers that… Read More »
Reminder: Secure your devices if you use them for U-M work
Security is everyone’s responsibility. If you use your personal devices—smartphone, laptop, tablet, and so on—for work, you are responsible for appropriately securing and managing them, as well as for meeting the obligations described in Security of Personally Owned Devices that Access or Maintain Sensitive Institutional Data (SPG 601.33). Your unit may have additional restrictions beyond those found in… Read More »
Change your password when you change your clocks
Have you changed your password(s) recently? When you change your clocks for the start of Daylight Saving Time on Sunday, March 12, consider changing your UMICH (Level-1) password as well. ITS suggests that you change your UMICH password every six months or so. An easy way to remember this is to change your password when you change your… Read More »
Dissonance Series – Privacy & Security Challenges in Investigative Journalism
Wednesday, March 22; 5:30–6:30 pm; Michigan League, Henderson Room. Join Knight-Wallace Fellows Bastian Obermayer and Laurent Richard as they discuss their work in investigating and reporting on the Panama Papers and Luxembourg Leaks. This discussion will focus on the privacy and IT security challenges in engaging in this high-profile, international investigatory journalism. Admission is free. Light refreshments included. The… Read More »
Integrity of voting systems still a concern
J. Alex Halderman, professor of computer science and engineering, received a lot of media attention in the days after the 2016 presidential election for voicing concerns about the integrity of electronic voting systems in the U.S. In this extensive interview with The Chronicle of Higher Education, Halderman, director of U-M’s Center for Computer Security and Society, contends that the initial reports… Read More »
Leaks, Whistleblowers and Big Data: Collaborative Journalism Across Borders
Monday, February 20 2017; 3- 5 pm; Rackham Graduate School (Horace H.) – Rackham Amphitheatre, fourth floor. Wallace House presents the investigative journalists behind The Panama Papers and Luxembourg Leaks. A panel of Knight-Wallace Fellows and the deputy director for The International Consortium of Investigative Journalists (ICIJ) will share the stories behind the biggest data leaks in history, the… Read More »
Forged emails sent to CoE groups
On Tuesday, February 7, forged emails carrying messages of hate were sent to several College of Engineering email groups from an anonymous email server. The messages were “spoofed” so they appeared to come from an engineering faculty member and a doctoral student. They did not send the messages. The U-M Police Department and the FBI are conducting a joint… Read More »
Cybersecurity forecast
Hacks and data breaches continue to make headlines—including during the presidential election—but that hasn’t seemed to worry consumers, or even many policymakers. M.S. Krishnan, the Accenture Professor of Computer Information at the Ross School of Business, says that while security breaches haven’t changed consumer behavior, it’s time for a cybersecurity summit. Krishnan, who is also professor of technology and… Read More »