Tax fraud prevention tips
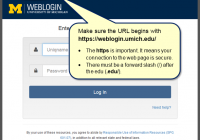
Beware: Identity thieves can file fraudulent tax returns in your name and steal your tax refund. Last year, criminals filed false returns for people across the nation, including several U-M employees. Information Assurance (IA) offers the following tips to help you protect yourself from identity theft and tax fraud: Turn on two-factor authentication for Weblogin to add extra… Read More »