Google Chrome verification begins May 7
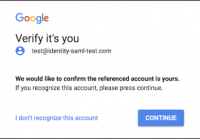
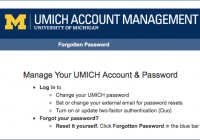
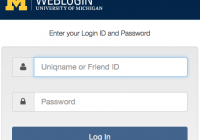
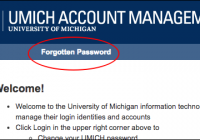
Beginning Monday, May 7, Google is rolling out a new security feature that requires users to verify their identity when using the Chrome browser to log in to Google at U-M. The information below explains what to expect with the new Google Chrome verification process. When you log in to your Google at U-M account using the Chrome… Read More »