Category Archives: Safe Computing
Plan now to attend SUMIT on October 29
Protecting U-M data and systems: Shared values and a community effort
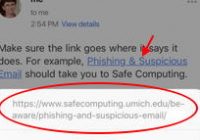
Check links on your smartphone before tapping
U.S. universities confront a security storm in Congress
Sol Bermann, U-M’s chief information security officer, is quoted in a recent article in “Science” magazine about legislation moving through Congress that aims to prevent foreign entities from taking unfair advantage of the traditionally open U.S. research system. Both House and Senate bills focus heavily on enhancing cybersecurity, seen as an essential tool in protecting intellectual property and… Read More »
Video: Interview with Sol Bermann, U-M CISO
Sol Bermann, executive director of information assurance and chief information security officer (CISO) for U-M, was recently interviewed by “EDUCAUSE Review” about the growing need for privacy management, the policies and laws in place to protect our privacy, and how big data has changed the game. In a wide-ranging interview, Bermann discusses: The difference between a chief privacy… Read More »
Better protection for U-M networks
ITS began implementing components of a greatly enhanced network security threat detection and mitigation system in late June. This approach combines cutting edge technologies, open source tools, and U-M’s MITN threat intelligence framework to provide a security solution that scales across U-M networks. It will allow ITS to: Detect and mitigate network threats across more U-M networks. Extend… Read More »
Secure your connection with a VPN
If you plan to use an internet connection to access U-M systems while off campus, you should secure your connection with a Virtual Private Network (VPN). When you use a U-M VPN, you are securely connected using a U-M network, regardless of where you are. This allows you to access U-M resources that require you to be on… Read More »
U-M IT security posture information published
Have external collaborators, granting agencies, or vendor partners ever asked you for information about the university’s IT security posture? ITS Information Assurance has pulled together an overview of how we secure U-M into one document to help you answer those questions: U-M IT Security Posture (U-M login required)Note: IT security and compliance is a shared responsibility. This document… Read More »
Reveal short URLs, use them with caution
Shortened URLs, such as those from bit.ly and goo.gl, make it easy to type in a web address quickly but hard to tell where your web browser will actually take you. Before clicking a shortened URL, check for the full URL. Most URL shorteners—including those used at U-M—include a preview feature. In addition, there are several URL checkers… Read More »
Dearborn to offer masters program in cybersecurity
Just two years after starting its bachelors in cybersecurity, UM-Dearborn is already adding a masters program. Associate Professor of Computer and Information Science Di Ma says the fall debut of the M.S. in Cybersecurity and Information Assurance is being driven by student demand and the metro region’s big growth in the field — which saw a 400-percent spike in job… Read More »
Review your MCommunity privacy settings
Your profile Your MCommunity profile shows only information related to your U-M affiliation. For U-M staff members, publicly viewable information includes: name, uniqname, email address, U-M affiliation, title, and U-M work phone number and address. You can choose privacy settings for additional information about yourself, such as your notice or description. You can choose whether the additional information… Read More »
Don’t reuse your UMICH password
You put U-M systems and data at risk if you use your UMICH (Level-1) password for non-university services. If you use your UMICH email address and password to establish a personal account (for example, at LinkedIn), and that information is exposed in a data breach, your UMICH account is now at risk. If you have used your UMICH… Read More »
HITS simulated phishing campaign continues through June
Beware of tech support scams
Have you ever seen a pop-up on your computer or received an unsolicited call urging you to contact “tech support?” Scammers sometimes impersonate IT support staff and claim something is wrong with your computer. They offer to help fix the problem—for a fee—but instead may steal your personal information or infect your computer with malicious software. This can… Read More »
Unhackable: New chip stops attacks before they start
A new computer processor architecture developed at U-M could usher in a future where computers proactively defend against threats, rendering the current electronic security model of bugs and patches obsolete. Called MORPHEUS, the chip blocks potential attacks by encrypting and randomly reshuffling key bits of its own code and data 20 times per second—infinitely faster than a human… Read More »
Transfer file ownership before people leave the university
When U-M employees leave the university or transfer from one unit to another, it is important to transfer ownership of files, MCommunity groups, and other digital resources needed for university business. See these resources for tips and information: Leaving U-M U-M Termination Checklist (downloadable Excel file from U-M Human Resources) Plan ahead to avoid disruptions and protect privacy… Read More »
Your role in implementing new info security standards
No matter what your job at U-M, you have a role to play in implementing the new information security standards and the revised Information Security (SPG 601.27) policy. Your responsibilities could include: Participating in data protection training Reporting suspected or actual IT security incidents Learning and using secure coding best practices Configuring systems to meet minimum security requirements… Read More »
Tips for writing emails that don’t look phishy
You have an important university email to send, but how do you craft it so it looks like the official, trustworthy, communication it is? In other words, how do you keep people from thinking it is a phish? Email users are rightfully suspicious of unsolicited email, but that can sometimes cause them to ignore or delete your important,… Read More »
UM-Dearborn implements encryption program
UM-Dearborn ITS has kicked off a new initiative to encrypt users’ endpoint devices (laptop and desktop computers). This effort dramatically improves the way UM-Dearborn secures its endpoints, and the data and services they touch. In addition, it helps bring campus in line with U-M IT security policies and standards. The effort initially rolled out to two departments that… Read More »