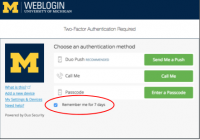
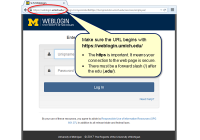
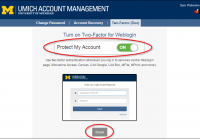
Duo can remember you for seven days
Now you can get the security benefits of two-factor for Weblogin with fewer login prompts. The Duo Remember Me time was extended from 12 hours to seven days on August 25. Remember to select the checkbox if you want Duo to remember you. You’ll see the Remember Me checkbox when you log in to a U-M site or… Read More »